I’m working on using the LdapIdentityProviderPlugin. It seems to work most of the way.
Here is my bpm-platform.xml
<plugin>
<class>org.camunda.bpm.identity.impl.ldap.plugin.LdapIdentityProviderPlugin</class>
<properties>
<property name="serverUrl">ldap://host.docker.internal:10389/</property>
<property name="acceptUntrustedCertificates">true</property>
<property name="managerDn">uid=jtsTestAdminUser,ou=People,dc=example,dc=com</property>
<property name="managerPassword">password1</property>
<property name="baseDn">dc=example,dc=com</property>
<property name="userSearchBase">ou=People</property>
<property name="userSearchFilter">(objectclass=person)</property>
<property name="userIdAttribute">uid</property>
<property name="userFirstnameAttribute">cn</property>
<property name="userLastnameAttribute">sn</property>
<property name="userEmailAttribute">mail</property>
<property name="userPasswordAttribute">userPassword</property>
<property name="groupSearchBase">ou=Roles,ou=RBAC</property>
<property name="groupSearchFilter">(objectclass=organizationalRole)</property>
<property name="groupIdAttribute">cn</property>
<property name="groupTypeAttribute">cn</property>
<property name="groupNameAttribute">cn</property>
<property name="groupMemberAttribute">roleOccupant</property>
<property name="sortControlSupported">false</property>
</properties>
</plugin>
<!-- LDAP CONFIGURATION -->
<!-- The following plugin allows you to grant administrator authorizations to an existing LDAP user -->
<plugin>
<class>org.camunda.bpm.engine.impl.plugin.AdministratorAuthorizationPlugin</class>
<properties>
<property name="administratorUserName">jtsTestAdminUser</property>
<property name="administratorGroupName">oamROLE1</property>
</properties>
</plugin>
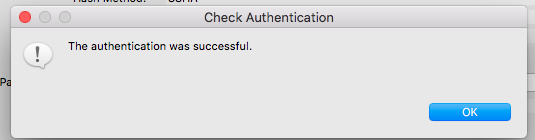
I’m able to log in as jtsTestAdminUser
and you can see my users:
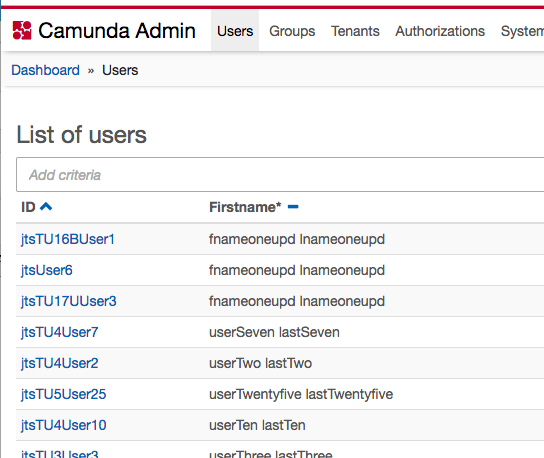
that are in my ldap
and you can see the groups.
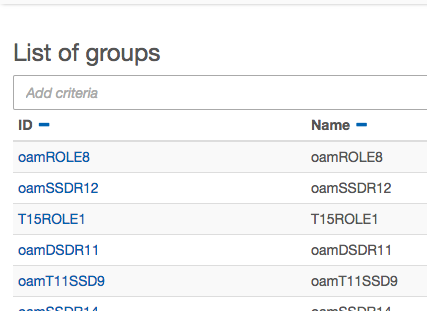
and you can see users in the groups.
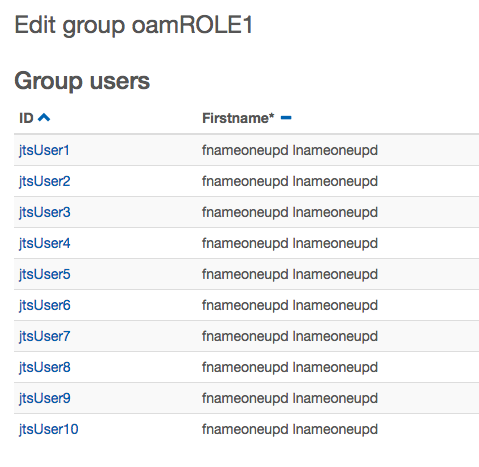
and the authorization to the group (plus I added a specific user)
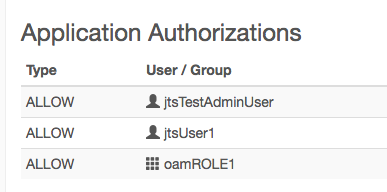
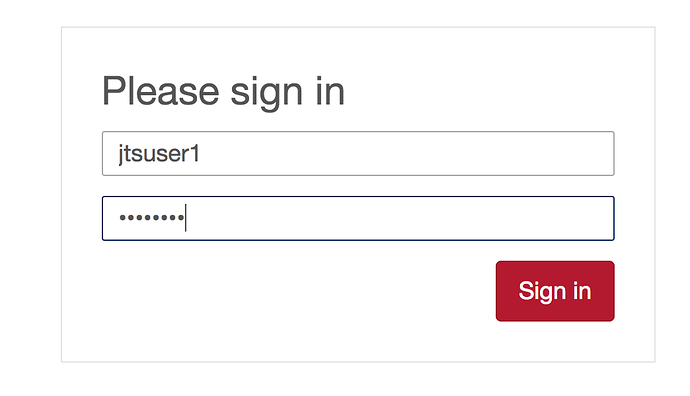
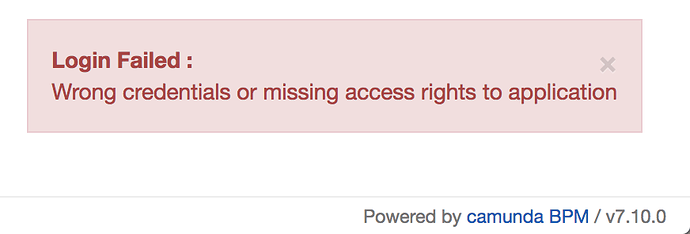
However, when I try to log in with jtsUser1/password (I set it write in my LDAP browser) login fails:
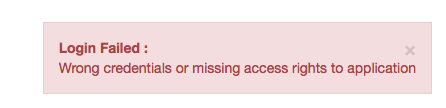
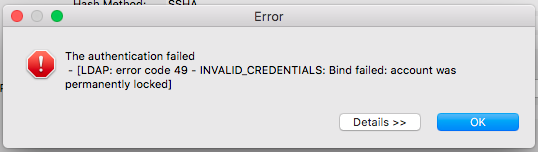
Please let me know how I could trouble shoot this, or how to fix. thank you!