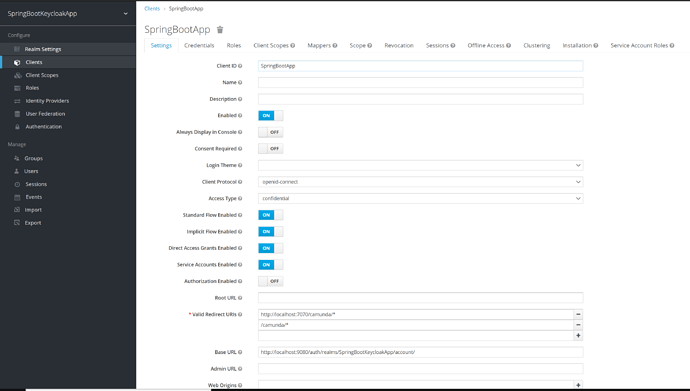
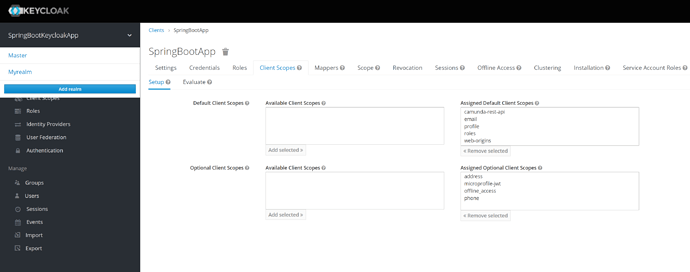
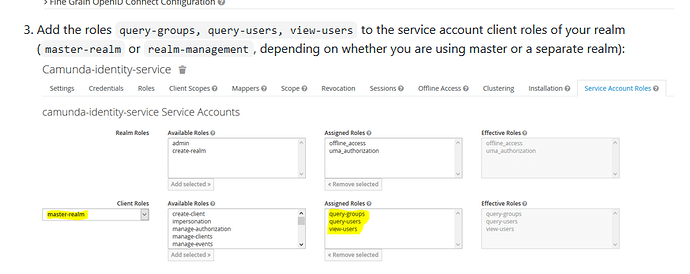
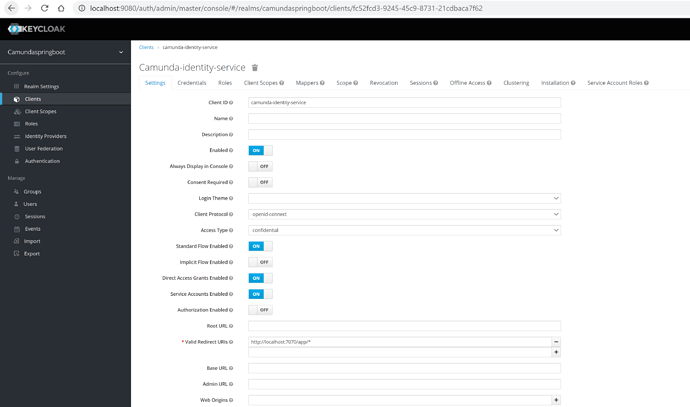
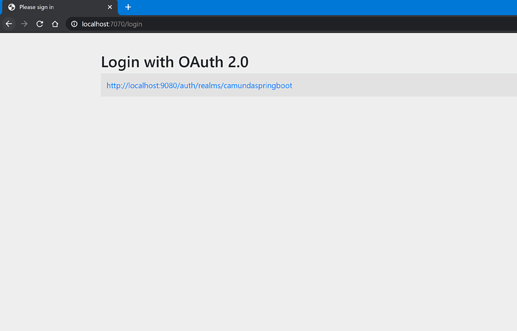
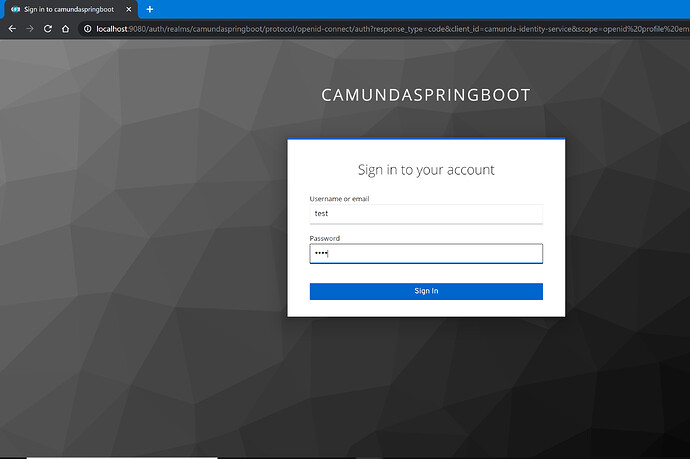
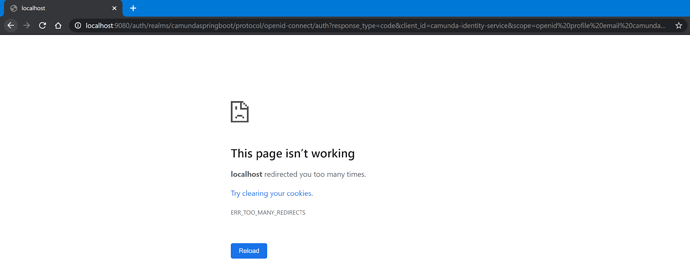
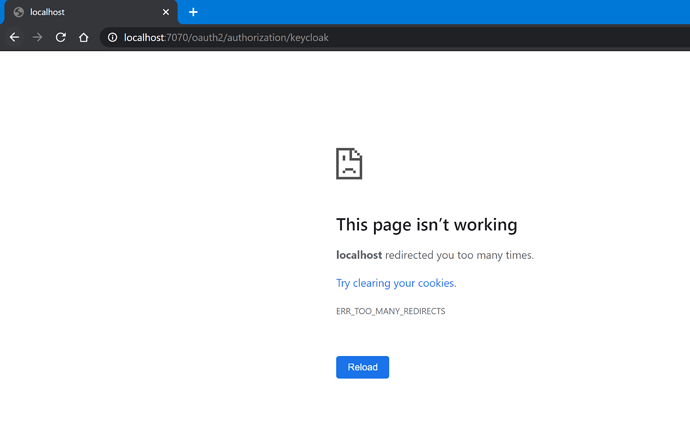
I was trying to run the following example. I create Client and Users in Keycloak… when i start the application the following error is shown.
Caused by: org.springframework.beans.factory.BeanCreationException: Error creating bean with name ‘processEngineFactoryBean’: FactoryBean threw exception on object creation; nested exception is org.camunda.bpm.engine.impl.identity.IdentityProviderException: Unable to query users
at org.springframework.beans.factory.support.FactoryBeanRegistrySupport.doGetObjectFromFactoryBean(FactoryBeanRegistrySupport.java:176) ~[spring-beans-5.2.9.RELEASE.jar:5.2.9.RELEASE]
at org.springframework.beans.factory.support.FactoryBeanRegistrySupport.getObjectFromFactoryBean(FactoryBeanRegistrySupport.java:101) ~[spring-beans-5.2.9.RELEASE.jar:5.2.9.RELEASE]
at org.springframework.beans.factory.support.AbstractBeanFactory.getObjectForBeanInstance(AbstractBeanFactory.java:1828) ~[spring-beans-5.2.9.RELEASE.jar:5.2.9.RELEASE]
at org.springframework.beans.factory.support.AbstractAutowireCapableBeanFactory.getObjectForBeanInstance(AbstractAutowireCapableBeanFactory.java:1265) ~[spring-beans-5.2.9.RELEASE.jar:5.2.9.RELEASE]
at org.springframework.beans.factory.support.AbstractBeanFactory.doGetBean(AbstractBeanFactory.java:334) ~[spring-beans-5.2.9.RELEASE.jar:5.2.9.RELEASE]
at org.springframework.beans.factory.support.AbstractBeanFactory.getBean(AbstractBeanFactory.java:202) ~[spring-beans-5.2.9.RELEASE.jar:5.2.9.RELEASE]
at org.springframework.beans.factory.config.DependencyDescriptor.resolveCandidate(DependencyDescriptor.java:276) ~[spring-beans-5.2.9.RELEASE.jar:5.2.9.RELEASE]
at org.springframework.beans.factory.support.DefaultListableBeanFactory.doResolveDependency(DefaultListableBeanFactory.java:1307) ~[spring-beans-5.2.9.RELEASE.jar:5.2.9.RELEASE]
at org.springframework.beans.factory.support.DefaultListableBeanFactory.resolveDependency(DefaultListableBeanFactory.java:1227) ~[spring-beans-5.2.9.RELEASE.jar:5.2.9.RELEASE]
at org.springframework.beans.factory.annotation.AutowiredAnnotationBeanPostProcessor$AutowiredFieldElement.inject(AutowiredAnnotationBeanPostProcessor.java:640) ~[spring-beans-5.2.9.RELEASE.jar:5.2.9.RELEASE]
… 85 common frames omitted
Caused by: org.camunda.bpm.engine.impl.identity.IdentityProviderException: Unable to query users
at org.camunda.bpm.extension.keycloak.KeycloakUserService.requestUsersWithoutGroupId(KeycloakUserService.java:276) ~[camunda-bpm-identity-keycloak-all-2.0.0.jar:2.0.0]
at org.camunda.bpm.extension.keycloak.KeycloakIdentityProviderSession.findUserByQueryCriteria(KeycloakIdentityProviderSession.java:130) ~[camunda-bpm-identity-keycloak-all-2.0.0.jar:2.0.0]
at org.camunda.bpm.extension.keycloak.KeycloakUserQuery.executeList(KeycloakUserQuery.java:38) ~[camunda-bpm-identity-keycloak-all-2.0.0.jar:2.0.0]
at org.camunda.bpm.engine.impl.AbstractQuery.evaluateExpressionsAndExecuteList(AbstractQuery.java:219) ~[camunda-engine-7.14.0.jar:7.14.0]
at org.camunda.bpm.engine.impl.AbstractQuery.executeSingleResult(AbstractQuery.java:241) ~[camunda-engine-7.14.0.jar:7.14.0]
at org.camunda.bpm.engine.impl.AbstractQuery.execute(AbstractQuery.java:195) ~[camunda-engine-7.14.0.jar:7.14.0]
at org.camunda.bpm.engine.impl.interceptor.CommandExecutorImpl.execute(CommandExecutorImpl.java:28) ~[camunda-engine-7.14.0.jar:7.14.0]
at org.camunda.bpm.engine.impl.interceptor.CommandContextInterceptor.execute(CommandContextInterceptor.java:110) ~[camunda-engine-7.14.0.jar:7.14.0]
at org.camunda.bpm.engine.spring.SpringTransactionInterceptor$1.doInTransaction(SpringTransactionInterceptor.java:46) ~[camunda-engine-spring-7.14.0.jar:7.14.0]
at org.springframework.transaction.support.TransactionTemplate.execute(TransactionTemplate.java:140) ~[spring-tx-5.2.9.RELEASE.jar:5.2.9.RELEASE]
at org.camunda.bpm.engine.spring.SpringTransactionInterceptor.execute(SpringTransactionInterceptor.java:44) ~[camunda-engine-spring-7.14.0.jar:7.14.0]
at org.camunda.bpm.engine.impl.interceptor.ProcessApplicationContextInterceptor.execute(ProcessApplicationContextInterceptor.java:70) ~[camunda-engine-7.14.0.jar:7.14.0]
at org.camunda.bpm.engine.impl.interceptor.CommandCounterInterceptor.execute(CommandCounterInterceptor.java:35) ~[camunda-engine-7.14.0.jar:7.14.0]
at org.camunda.bpm.engine.impl.interceptor.LogInterceptor.execute(LogInterceptor.java:33) ~[camunda-engine-7.14.0.jar:7.14.0]
at org.camunda.bpm.engine.impl.AbstractQuery.executeResult(AbstractQuery.java:160) ~[camunda-engine-7.14.0.jar:7.14.0]
at org.camunda.bpm.engine.impl.AbstractQuery.singleResult(AbstractQuery.java:136) ~[camunda-engine-7.14.0.jar:7.14.0]
at org.camunda.bpm.spring.boot.starter.configuration.impl.custom.CreateAdminUserConfiguration.userAlreadyExists(CreateAdminUserConfiguration.java:93) ~[camunda-bpm-spring-boot-starter-7.14.0.jar:7.14.0]
at org.camunda.bpm.spring.boot.starter.configuration.impl.custom.CreateAdminUserConfiguration.postProcessEngineBuild(CreateAdminUserConfiguration.java:60) ~[camunda-bpm-spring-boot-starter-7.14.0.jar:7.14.0]
at org.camunda.bpm.engine.impl.cfg.CompositeProcessEnginePlugin.postProcessEngineBuild(CompositeProcessEnginePlugin.java:107) ~[camunda-engine-7.14.0.jar:7.14.0]
at org.camunda.bpm.engine.impl.cfg.ProcessEngineConfigurationImpl.invokePostProcessEngineBuild(ProcessEngineConfigurationImpl.java:1267) ~[camunda-engine-7.14.0.jar:7.14.0]
at org.camunda.bpm.engine.impl.cfg.ProcessEngineConfigurationImpl.buildProcessEngine(ProcessEngineConfigurationImpl.java:974) ~[camunda-engine-7.14.0.jar:7.14.0]
at org.camunda.bpm.engine.spring.SpringTransactionsProcessEngineConfiguration.buildProcessEngine(SpringTransactionsProcessEngineConfiguration.java:67) ~[camunda-engine-spring-7.14.0.jar:7.14.0]
at org.camunda.bpm.engine.spring.ProcessEngineFactoryBean.getObject(ProcessEngineFactoryBean.java:55) ~[camunda-engine-spring-7.14.0.jar:7.14.0]
at org.camunda.bpm.engine.spring.ProcessEngineFactoryBean.getObject(ProcessEngineFactoryBean.java:34) ~[camunda-engine-spring-7.14.0.jar:7.14.0]
at org.springframework.beans.factory.support.FactoryBeanRegistrySupport.doGetObjectFromFactoryBean(FactoryBeanRegistrySupport.java:169) ~[spring-beans-5.2.9.RELEASE.jar:5.2.9.RELEASE]
… 94 common frames omitted
Caused by: keycloakjar.org.springframework.web.client.HttpClientErrorException$Forbidden: 403 Forbidden: [{“error”:“unknown_error”}]
at keycloakjar.org.springframework.web.client.HttpClientErrorException.create(HttpClientErrorException.java:109) ~[camunda-bpm-identity-keycloak-all-2.0.0.jar:2.0.0]
at keycloakjar.org.springframework.web.client.DefaultResponseErrorHandler.handleError(DefaultResponseErrorHandler.java:184) ~[camunda-bpm-identity-keycloak-all-2.0.0.jar:2.0.0]
at keycloakjar.org.springframework.web.client.DefaultResponseErrorHandler.handleError(DefaultResponseErrorHandler.java:125) ~[camunda-bpm-identity-keycloak-all-2.0.0.jar:2.0.0]
at keycloakjar.org.springframework.web.client.ResponseErrorHandler.handleError(ResponseErrorHandler.java:63) ~[camunda-bpm-identity-keycloak-all-2.0.0.jar:2.0.0]
at keycloakjar.org.springframework.web.client.RestTemplate.handleResponse(RestTemplate.java:782) ~[camunda-bpm-identity-keycloak-all-2.0.0.jar:2.0.0]
at keycloakjar.org.springframework.web.client.RestTemplate.doExecute(RestTemplate.java:740) ~[camunda-bpm-identity-keycloak-all-2.0.0.jar:2.0.0]
at keycloakjar.org.springframework.web.client.RestTemplate.execute(RestTemplate.java:674) ~[camunda-bpm-identity-keycloak-all-2.0.0.jar:2.0.0]
at keycloakjar.org.springframework.web.client.RestTemplate.exchange(RestTemplate.java:583) ~[camunda-bpm-identity-keycloak-all-2.0.0.jar:2.0.0]
at org.camunda.bpm.extension.keycloak.KeycloakUserService.requestUserById(KeycloakUserService.java:352) ~[camunda-bpm-identity-keycloak-all-2.0.0.jar:2.0.0]
at org.camunda.bpm.extension.keycloak.KeycloakUserService.requestUsersWithoutGroupId(KeycloakUserService.java:224) ~[camunda-bpm-identity-keycloak-all-2.0.0.jar:2.0.0]
… 118 common frames omitted